When you are working in IT industry, you will sooner or later hear about the OSI model.
The Open Systems Interconnection model (OSI model) is a conceptual model that characterises and standardises the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology.
Source: Wikipedia
The OSI model is a tool, a framework which splits the way data takes into seven abstraction layers: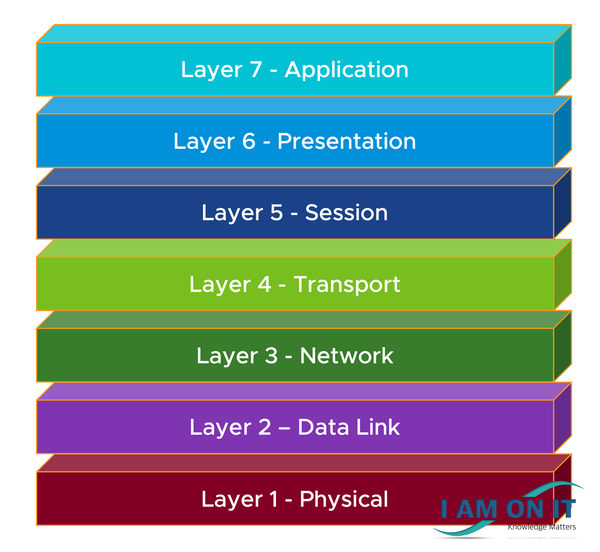
Each of the layers hides the details from the layer below from the layer above (e. g. layer 3 does not know details from layer 1, as layer 2 hides those details).
Layers have different features assigned and there are protocols or technologies associate with each of the layers.
Taking a look at the OSI layers, starting from bottom (layer 1 – physical) to top (layer 7 – application).
Layer 1 – Physical
As the name of the layer gives it away – it’s the physical part of the system, e. g. network cables, power plugs. But also, the electrical characteristics of signals transmitting data from node A to node B are specified here.
Layer 2 – Data Link
The layer provides data transfer between nodes which are directly connected. Also, basic error detection and correction is provided in the layer.
In the data link layer, you also have the sub layer media access control (MAC) layer and the sub layer logical link control (LLC). The MAC address is the unique hardware address of a device. The LLC can be seen as an interface between MAC and layer 3, the network layer.
Layer 3 – Network
In this layer the logical addressing is one of the functions provided. The layer also manages the communication between devices – aka routing.
IP and IPX are the most popular layer 3 protocols. IP is usually paired with TCP and IPX with SPX.
Layer 4 – Transport
This layer is the layer where one computer on the network communicates with another computer. The data transfer between the network computers is coordinated here. Multiple connections are simultaneously managed.
The protocols TCP and UDP are operating in this layer.
Layer 5 – Session
The layer is responsible for establishing, maintaining and terminating the links between two network computers. Without a link, no communication can take place.
Alternatively, UDP, an efficient, sessionless and connectionless protocol, poses a different set of security risks and should not be utilized in security relevant cases.
Layer 6 – Presentation
This layer ensures that the data sent is compatible with the lower layers but also that the data is acceptable for the receiving end of the communication link.
Layer 7 – Application
This is the top layer in the OSI model. It’s the closet layer to the user.
The name – application – might be a bit misleading as applications, e. g. web browsers, do not reside on this layer but rely on the communication on this layer.
The most known protocol in this layer is HTTP. If you use the internet, you use HTTP to access web sites.
A mnemonic to remember the layers of the OSI model – bottom to top:
Please Do Not Throw Salami Pizza Away.
On a funny side note: Sometimes you might hear someone talking about layer 8. There is no layer 8 in the OSI model, but there is a layer 8 :-D. Layer 8 is usually a synonym for the end user. Because if something is not working but no technical issues can be found, layer 8 might cause the issue themselves. I have been there myself – a layer 8 :-D.
Sources used:







